- Sap Secure Login Server Installation Guide
- Secure Server Webmail
- Secure Login Server Sap
- Secure Login Server Sap Server
- Secure Server Logon Screen
Symptom
Is it mandatory to run SAP SSO Secure Login Server (SLS) 3.0 on its own dedicated JAVA stack? Or can we piggy back SLS on an existing SAP JAVA stack solution such as our Process Orchestration stack? Hardware isn't an issue, but I'd prefer to reduce the growing number of instances in our environment. Logging into the Secure Login Client SPNEGO profile results in the error: 'Supplied credentials not accepted by the server.' If the traces show the below errors, go to Resolution point 1. Secure Login Client traces: 'Got kerberos ticket for 'HTTP/' with server key type 18 and session key type 18'. 'Cli-00000003: Cannot perform client authentication: Have no certificate fitting to CA names received from server'.
- Logging into the Secure Login Client SPNEGO profile results in the error:
'Supplied credentials not accepted by the server.' - If the traces show the below errors, go to Resolution point 1.
Secure Login Client traces:
'Got kerberos ticket for 'HTTP/<SPN>' with server key type 18 and session key type 18'
'Cli-00000003: Cannot perform client authentication: Have no certificate fitting to CA names received from server'
AS Java traces:
'Could not validate SPNEGO token. Reason: Checksum error.
No logon policy was applied' - If the AS Java traces show the below error, go to Resolution point 2.
'
Could not validate SPNEGO token.
[EXCEPTION]
java.lang.Exception: Clock skew too great. Client time: <>
'
 Read more...
Read more... Environment
Sap Secure Login Server Installation Guide
Product
Keywords
SLC, SecureLoginDefaultPolicyConfigurationSPNEGO, SPNegoLoginModule, Secure Login Server, SLS, default, developer, AD, Active Directory, service user, account, clock, application server, failed , KBA , BC-IAM-SSO-SL , Secure Login , Problem
About this page
This is a preview of a SAP Knowledge Base Article. Click more to access the full version on SAP ONE Support launchpad (Login required).Search for additional results
Visit SAP Support Portal's SAP Notes and KBA Search.
Great post Stephan, thanks a lot 😎
Secure Server Webmail
I got one question in regards to the Remote CA feature which isn’t clearly to me.
Secure Login Server Sap
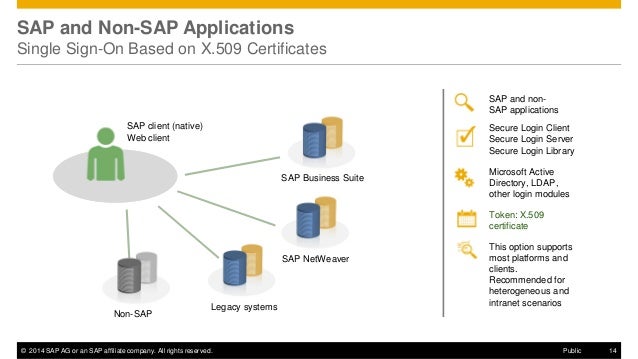
Using SLS one is able to define a custom certificate layout, same in other CAs like the supported ADCS where this is done by creating custom certificate templates. However the user mapping features in ADCS are somehow limited and not as flexible as in the SLS. The SLS has these nice little „user name mapping features“ allowing a company to include details of the authenticated End-Entity like various LDAP/AD attributes and maybe others, in oder to construct the certificate subject name or additional extensions such as the subject alternative name with a value of choice.
Secure Login Server Sap Server
Given the fact one has enabled Remote CA, that means the SLS is now acting as a intermediary between the End-Entity and the signing CA e.g. ADCS. As a registration authority i understand, the SLS is still responsible to authenticate the End-Entity thus still with the unchanged feature set allowing him to enrich the received certificate request with additional information about the requester.
The CA trusts the SLS-RA, receives the „modified“ PCKCS#10 signature request from SLS, somehow wrapped inside CMS or by other means, sent from SLS to CA via enrollment web service or CMC using HTTP/TLS as a transport layer. All fine.
Now based on the CA certificate policies, certificate template design etc. the CA may be able to use the additional user name attributes part of the CSR and just signs the certificate or maybe just not, because it does not meet the policy and the request will be denied by the CAs policy module. Do you already have some experiences when it comes to those user mapping scenarios e.g. instead using the Fully Distinguished Name or Display Name as the subject of a user certificate, to use a custom CN attribute in the subject? Hope I will soon have the chance to make my first project experience with that long-awaited Remote CA feature 😉
Secure Server Logon Screen

Cheers, Colt
